[ originally posted on Main Blog (posts organized by category) ]
DISCLAIMER: Not yet able to recommend outside experienced Linux users and tinkerers. Those who don’t mind fixing things on their own. Pinephone is still in relatively early stages and not yet ready for most users to attempt as a daily driver.
I use mine as a daily driver, and it’s the right choice for the right person. Always wanted a Linux computer, in my pocket. And it does receive calls/sms.
Think of Pinephone more as a Linux computer in your pocket, with capability to act as a phone (Computer-like in all things considered: battery life, software).
The channel has quite a few Pinephone videos (See 72 videos Pinephone Playlist).
The goal: Introduce other Linux aficionados to promising open source (focused) alternatives to the main 2 proprietary Smartphone OS options.
Long-term centralization takes the choice out of our hands. When staying with 2 closed off, closely aligned ecosystems, we can expect to live in whatever box they wish to build for us. [ such a box may become increasingly restrictive/intrusive to tech freedoms/liberties ]
(Innovation goes direction of funding)
For a Tech Freedom future.
Right now the Pinephone, Librem5, Fairphone, Pro1 X are a few of the main projects deserving attention/support to get us there: open source Smartphone.
A few of the main (currently maintained) Linux Pinephone Operating Systems:
- Arch (DanctNIX)
- Mobian (Debian Mobile)
- PostmarketOS (Alpine)
- Ubuntu Touch
- Manjaro
- (If you want me to add another currently maintained Pinephone OS, leave a comment here or on channel and I will be happy to add it)
In The Beginning There Was The N900:

The N900: Linux phone cult classic!
Ran surprisingly well (according to users- wasn’t lucky enough to try one).
Back to the topic of conversation:
PINEPHONE IDEAS IN PRACTICE:
Today’s video (Pinetab for the larger display- same underlying hardware/software/OS) covered a few of the basics (off top of my head). This article expands with additional recommended videos. Video was off the cuff, missing a few things I wanted to include.
The above video lists:
- Keep front camera switch off (most do not use this camera: back camera carries more MP)
- Turn off WiFi/Bluetooth switch when not in use (wipri is an option for wifi use, bluetooth should stay off when not in use)
Using Switches Demo (Household Item):
https://youtu.be/VFX4WbtpGRI
- Keeping microphone switch off (TIP: use earbuds with built in microphone for calls/microphone usage to allow switch to ensure microphone is never hijacked for advertising tracking/backdoor communication)
- Battery is removable: can be considered an added benefit in this world of closed off/locked down “innovations” (such as phones carrying soldered or glued in batteries)
- Replace stock modem firmware with something more open
- Tor Browser (See .desktop file for Mobian and instructions here; Video instructions HERE)
- Zulucrypt: excellent encryption program found on many of the top privacy/security Linux distributions (see video demo down below)
Zulucrypt Pinephone Demo Tutorial/Video:
https://youtu.be/87yg8peq3kw
Add Privacy-Redirect Extension for Tor Browser + Firefox:
Privacy-Redirect Extension automatically redirects:
Twitter/Youtube/StreetMaps/Wikipedia/Translation links to front end proxies.
When you install this into Tor Browser it can even redirect you to Tor Hidden Service (.onion) Front ends. See more in the video below:
WIPRI
First thing I install on a new device/Linux operating system (as we live in a world where department stores and others run wifi device sniffing tracking beacons- sometimes to deliver ads based on shopping location: other times to sell location history to data brokers). This ensures the mac address (and other metadata) do not leak to tracking (static hostnames may be an issue on public wifi when tied to other data sold to data brokers).
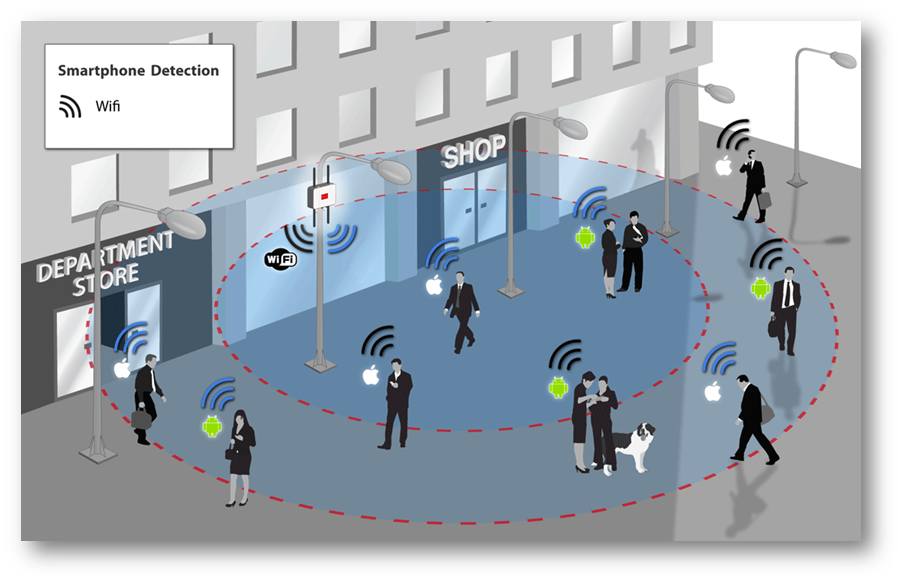
Some of these wifi device tracking systems share/sell mapped out tracking data history to data brokers. More on this in future videos.
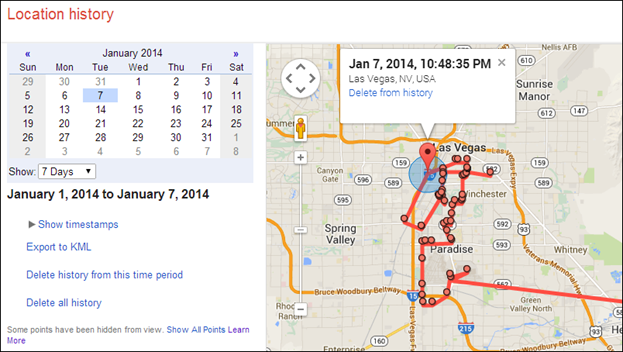
A more public example of this type of tracking is wigle.
See my python script ‘mactrack’ to see a demo of how these packets can be organized to track via signal strength (trilateration via multiple nodes) and the related wipri -s setting below.
MACtrack was written for the Pinephone: activating the button sets WiFi into “sniffing” mode, collecting closeby wifi devices, their brand name/mac address, signal strength (helps estimate distance), and device history of saved SSID’s.
It takes advantage of the cellular modem to then allow lookups of SSID location on wigle.
MACtrack is meant to serve as an example: showing information our devices give off. And a reminder to change your home router’s SSID.
Additionally can track home devices that frequently become disconnected (potential security risk if attackers collect those reconnect handshakes for wifi cracking). If you see your home devices on mactrack: they should be moved to a closer location to the router (or add a wifi extender).
MACtrack in action:https://www.youtube.com/embed/Qr-tTC5nQKE
BACK TO WIPRI:
Expanding on bullet #2, WiPri Recommendations: -p for home static smartphone mimic and -P for traveling (continuously changing Apple/Samsung mac addresses at continously changing times/mac addresses to help thwart off wifi sniffer trackers)
(Second recommendation option [for privacy geeks] -a mode to synchronize simultaneous continuously changing random mac addresses + signal strengths + hostnames at continuously changing randomized times).
The rest of the options available to try on Pinephone:
WiPri OPTIONS:
USE:
wipri -d [device] -r [randomizes mac continually changing times/addresses]
-p [Samsung/Apple: mac address mimic (static hold)] -P [Android/iPhone mac addresses mimic (continually changing times/addresses)] -a [continually randomize MAC, hostname, signal variations] -m [Static MAC] -i [new MAC identity] -h [rand hostname] -H [restore prev hostname] -s [random signals] -A [randomized WiFi mac + signal strength + hostname at continually changing times]
Features:
-d sets your device.
-r continually randomizes your mac address at randomly generated, continually changing random MAC addresses/times.
-p Android/iPhone mimic mode: sets single static identity: randomly generated valid mac address of either Apple or Android.
-P Android/iPhone mimic mode: continually changing randomized Samsung/Apple mac address changes- continually changing, at randomized changing times, using continually changing, randomized yet valid OUI Apple/Samsung mac addresses (this setting allows you to appear to WiFi trackers/sniffers [like KISMET] at any given time, as either an Android or iPhone;
-m [mac here] sets a mac address of your choice, holds it for remainder of running (checks to ensure firmware does not reset it)
-h change hostname to generic yet unique and completely random hostname. Using a generic base with random extension at the end of it.
-R restore previously held hostname
-H prints help; print out wipri command examples
-i generates a valid OUI based mac identity
-s txpower randomizer (experimental) randomizes the txpower of your device. This confuses certain WiFI trackers that determine location by signal strength.
-a anonymous mode: launch coordinated random changes: each change happens simultaneously: when the mac address changes so does the hostname and txpower/signal. This is intended to simulate new devices and changing locations. All 3 changes happen simultaneously, at changing, randomized times.
Easy WiPri install script Pinephone demo:https://www.youtube.com/embed/1j-AtFtsqH4
If you have questions on WiPri, leave a comment at the bottom of the page.
FIREJAIL TO PROTECT PINEPHONE PRIVACY:https://www.youtube.com/embed/bXRa9aYWcIY
For more on Firejail, see my other Firejail video HERE.
PINEPHONE PRIVATE MESSAGING RECOMMENDATIONS:
SIGNAL CLONE (AXOLOTL – CHECK CURRENT STATUS ON THIS ONE):https://www.youtube.com/embed/Wf64kPxs2Tk
DINO END-TO-END ENCRYPTED MESSENGER (XMPP + PGP/OMEMO):
I love using Dino, it runs rather well on the Pinephone. Many interesting XMPP chatrooms, and a nice, clean interface. https://www.youtube.com/embed/MyvBmO0tQGc
DISK ENCRYPTION:
Disk encryption carries multiple benefits.
Scenario: You lose your phone. If it’s encrypted, and off, encryption can prevent identity theft (via information/personal documents/identification) or passwords, personal banking information, etc.
In addition to protecting from data theft, encryption protects the integrity of your files. If your device is off/encrypted, no one can modify encrypted files to cause you harm.
Many Linux Phone operating systems come with the option to fully encrypt your disk on installation.
I suggest taking advantage of these options.
CRYPTO_HOMES:
Additionally for fun I wrote a script called “crypto_homes” where you can automate the entire process of encrypting your /home directory.
Not only does crypto_homes encrypt your /home directory to an sdcard + sets up boot (leaving original for easy reverts back), it automatically creates a hardware keyfile on a usbstick.
Simply put in the sdcard (for the encrypted home storage location), insert the usbstick, and run crypto_home.sh.
You will then be able to select any cipher (compiled into your kernel) and set the devices. From here you will be left at a crypthome> shell. Here you can overwrite disks or automate the process of creating an sdcard encrypted /home + usbstick key.
The idea: To allow as many encrypted virtual home sdcards as you like (attached to usbkey)
When I get more time, planning other options to manage multiple sdcards.
Crypto_homes video usage demo here:https://www.youtube.com/embed/Z9txf11RCt0
Take a look at crypto_homes so far here.
For Even More Privacy Tips/Tutorials Check Out The “Privacy” tab of posts/videos:
https://www.buymeacoffee.com/politictech/posts
Are all these steps really necessary?
Absolutely not.
They are options.
Demonstrations of a few things Linux phones can do. 🙂
(Try accomplishing all of the above in one of the 2 main closed off ecosystem!)
I’m always looking at/sharing ways we can help protect ethical Human Rights into the future.
We know not what the future may hold or how our data will be used into that future.
Privacy is declared a Universal Human Right in the United Nations Universal Declaration of Human Rights:
Article 12
No one shall be subjected to arbitrary interference with his privacy, family, home or correspondence, nor to attacks upon his honour and reputation. Everyone has the right to the protection of the law against such interference or attacks.
SEE REST OF CURRENT PINEPHONE VIDEOS FOUND ON THE PINEPHONE PLAYLIST
If you appreciated this content, Sharing of posts/videos is appreciated.
Support options found at the bottom of this page:
Sharing this content is very much appreciated.
FOLLOW:
VIDEO MIRRORS:
Youtube Odysee Bitchute Peertube
SUPPORT/DONATION OPTIONS:
CASHAPP:https://cash.app/$HumanRightsTech
BMAC: https://www.buymeacoffee.com/politictech/ (Donation Options + Support Services)
BTC: 3QDdTcLwLTPXKMBp5dLUhKJG6KbDxWsYWS
XMR:481wHzXEsW9E519uu3SiynMuGe1yUT43iiJ8M49fgxfngHr9MUPVNAmPgyjS4XYtvzD1TbK7P5ywUWhGo11ibT2RQhEcRSX
One thought on “Pinephone Privacy Ideas/Tips [Videos/Writeup]”