DISCLAIMER: video covers very recent whistle blower report.
Allegations still require looking into, and are not considered proof of “intent”.
Share the video / article.
Originally posted at BMAC Politictech Blog (posted here early)
TWITTER WHISTLEBLOWER: MUDGE (L0pht / cDc)
VIDEO COVERS:
What do I need to know?
What are the privacy implications?
How many employees have access to sensitive user data?
Were there user privacy compromises (this year) at Twitter?
Was SMS 2FA abused (this year) for mobile phone surveillance?
Who is this ‘Mudge’ guy? Why should we listen to him?
📰 FIND OUT THIS AND MORE.
📺 IN TODAY’S VIDEO:

(watch on 🧅 Tor Friendly, decentralized Peertube by clicking above image)
Watch Inside Post:https://www.youtube.com/embed/xS2jzX7Ace8
🔗 THANKS FOR SHARING (one way to support is sharing links on Social Media, Telegram…)
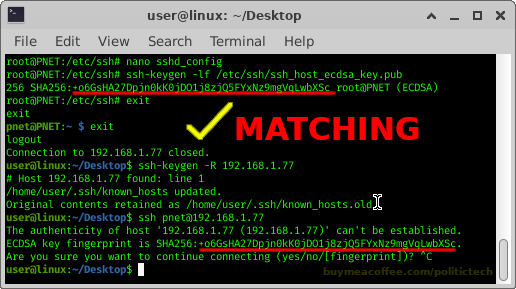
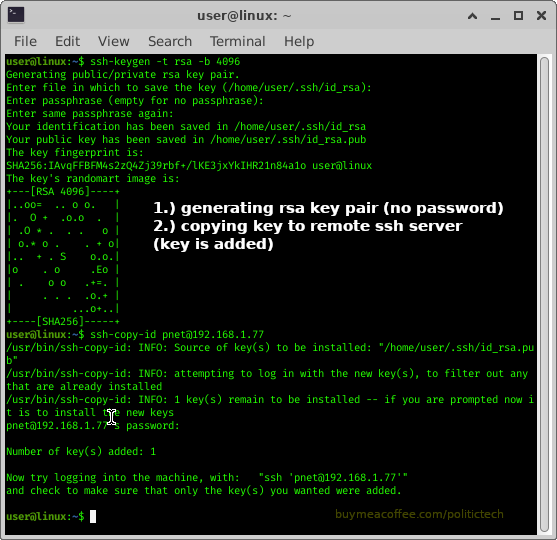
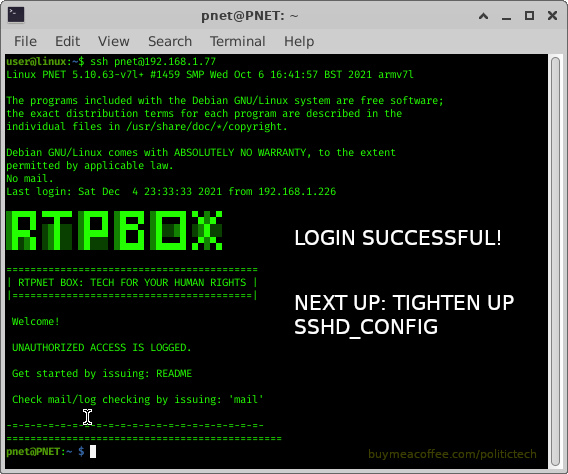
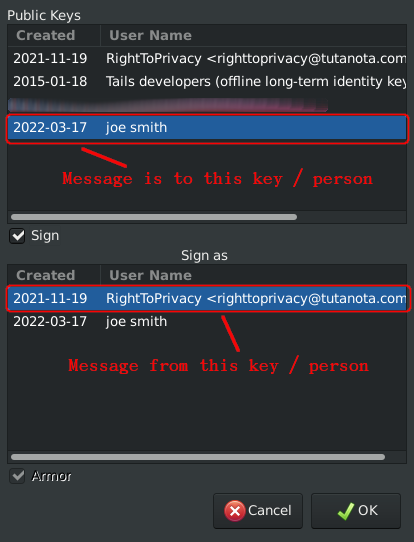
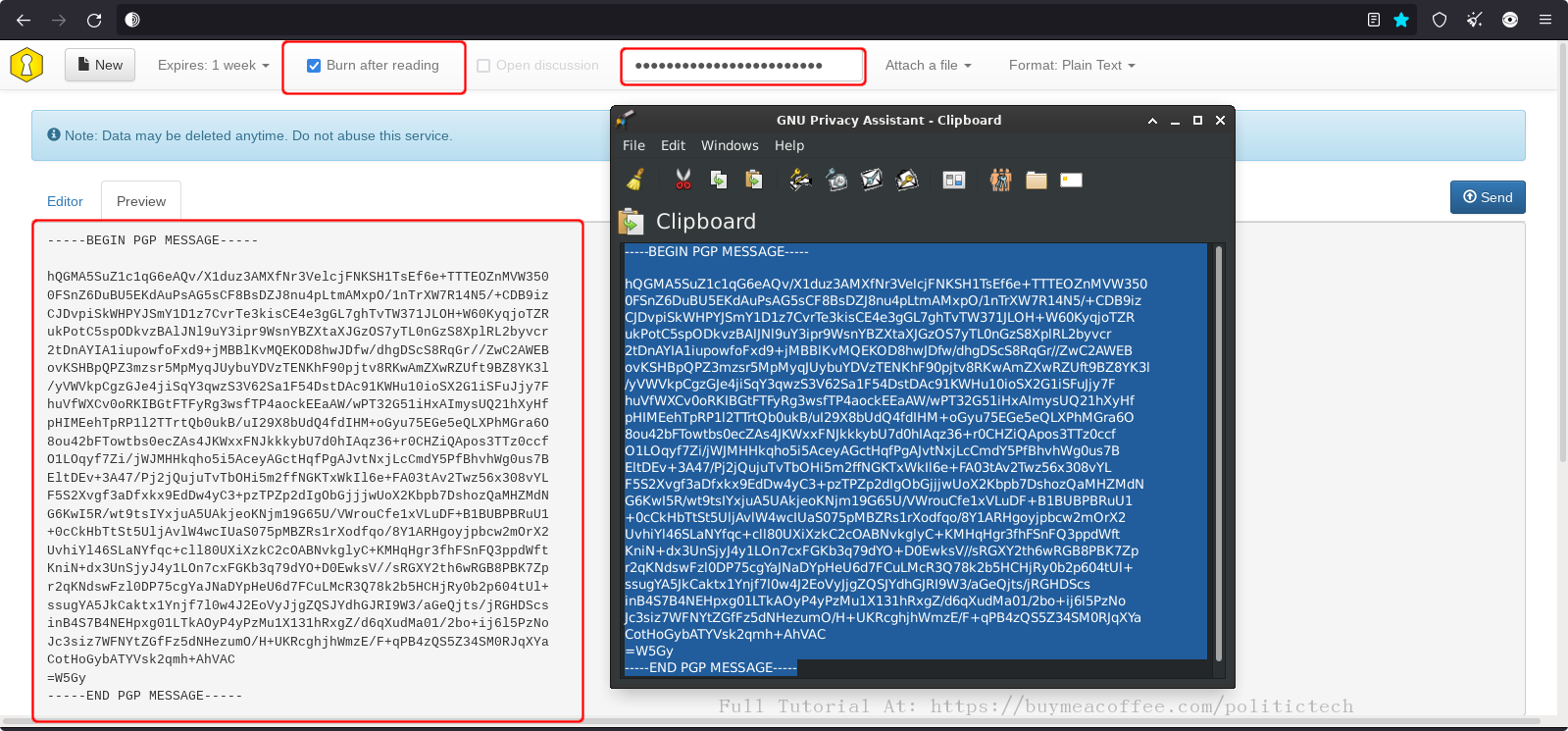
(below, I share screenshots I put created, underlining key points)
WHISTLEBLOWER REPORT HIGHLIGHTS IMPORTANCE OF ANONYMITY ON SOCIAL MEDIA:


EARLIER 2022 STORIES OF CONCERN
Firehose Data Allows Real-Time Tracking (2022)


Mitto AG Abused SMS 2FA For Mobile Surveillance (2022)

TIP: Use a dedicated email for social media accounts. Don’t use the same email or phone number you have connected to a bank, or “big tech” platform accounts. Every account sharing information can be neatly linked together.
🛡️ Twitter Introduces A New Phone Number Badge
This ‘badge’ will allow users to demonstrate they have a phone number connected to their account.
I see no problem with this, as long as phone numbers stay voluntary. Although it could potentially open certain users up (with this badge) to more likely attacks (earlier bug: phone number reveal).
Given information covered in the above video, requiring a phone number / identification would create a serious safety risk to activists, journalists, lawyers, and others in a sensitive position.
Not only does a phone number tie directly to a user’s identity (more reliably so than other means), it also opens them up to a host of new targeted “spear phishing” attacks.
The whistleblower report states up to 5,000 Twitter employees have access to sensitive user data. And, a Twitter employee was arrested for using their access to spy for the Saudi gov.
A country that executes its own dissidents.
There is no “safe” way for activists to share their phone number (or other personally identifiable information).
Email would make for far more secure form of 2FA, with an added bonus of protecting user identity, personal safety.
Regardless of the whistleblower report, I do hope Twitter remains a success. As long as it remains a place allowing free flows of information.
The only way this remains possible is if anonymous accounts are allowed to stay. As long as they are, I will continue to support Twitter over other mainstream Social Media platforms
(this way your data remains in your hands, depending on practices).
🧅 🔒 Twitter Now Has A Tor Hidden Service Onion Address

This one is a great move by Twitter. Nothing but good things to say about it.
Follow me on Twitter (onion), here.
TAKEAWAY:
We live in a world where power has become increasingly centralized…
🌎 A world where data contractors / monopolies can abuse access, power.
Simply Put: We simply can’t trust our personal data in the hands of strangers. No matter who they may work for.
When one has enough data, especially biometric data, one can use this in combination with AI, media, and various sensory applications / targeted experiences, to engineer future human behavior.
This is the very real future we are looking at. Don’t underestimate the power of data.
It’s why this page exists. Privacy (moreso anonymity) is vital to a free society, where people hold the power.
TIP: By proxying most of your internet data into mixnets, I2P / Tor (and newer options like Lokinet), you can make that data useless (instead of identifying).
Think of Tor as a haystack. Instead of the normal circuit your network packets route, Tor uses multiple layers of mixing / encryption to mix Tor browser client data into
In this world of increase, truly “free speech” cannot exist without the ability for anonymity.
💎 THANKS FOR SUPPORTING / SHARING THIS
Do You Think Twitter Really Fired Mudge For The Reasons They Stated?
NEXT: SHARE YOUR THOUGHTS